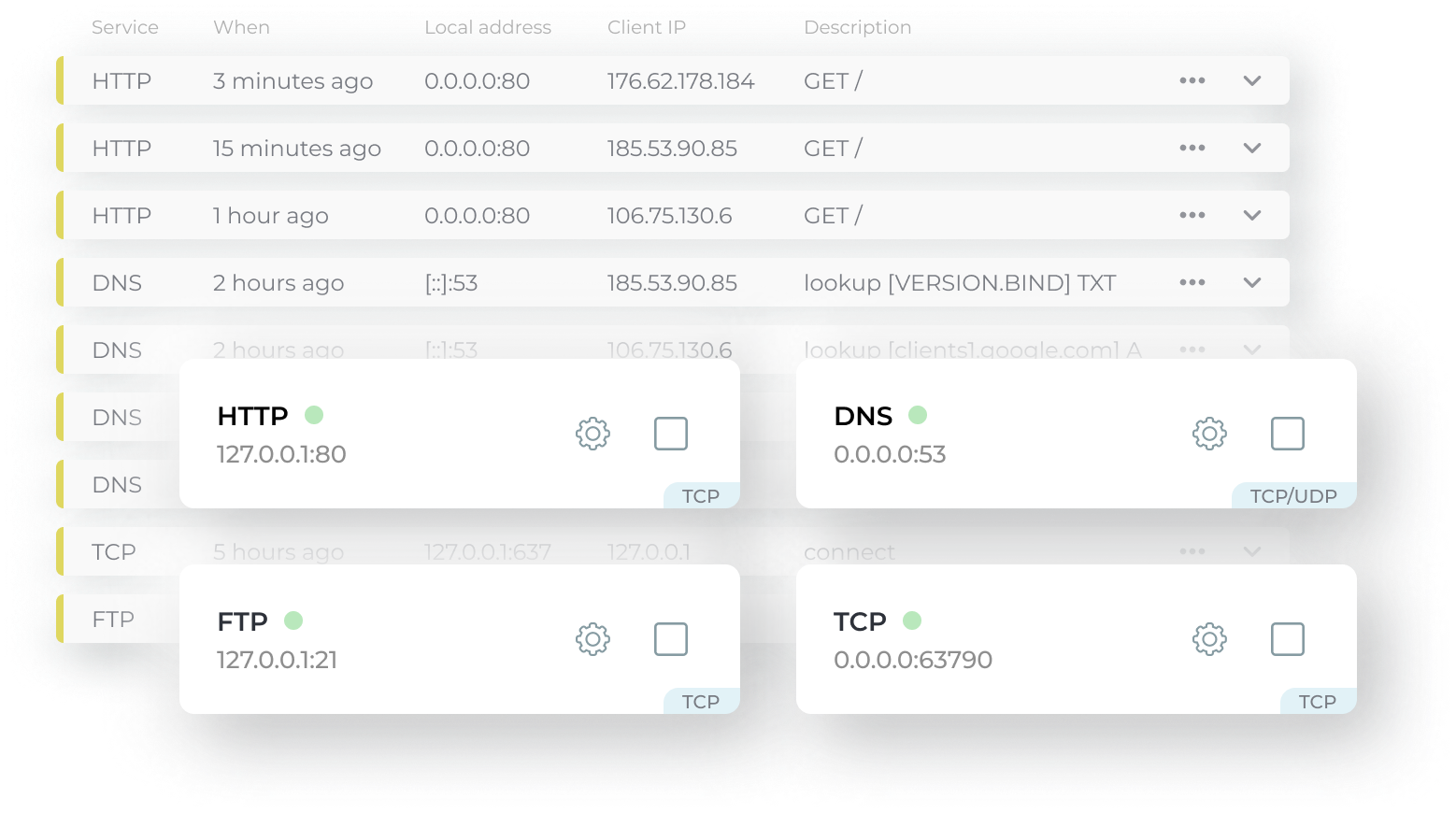
New vulnerabilities appear every day through which attackers can hack your application.
We catch attacks and provide you with access to data on all popular CVEs.
Know
All events are publicly available. You always have the opportunity to view the statistics on the exploitation of a particular CVE.
Anticipate
Use our IP lists to block attackers before they hack your resource.
Learn
Expand your knowledge based on data attached to events. All attacks from real life. You can see the requests of attackers in the original form.
How do you detect attacks?
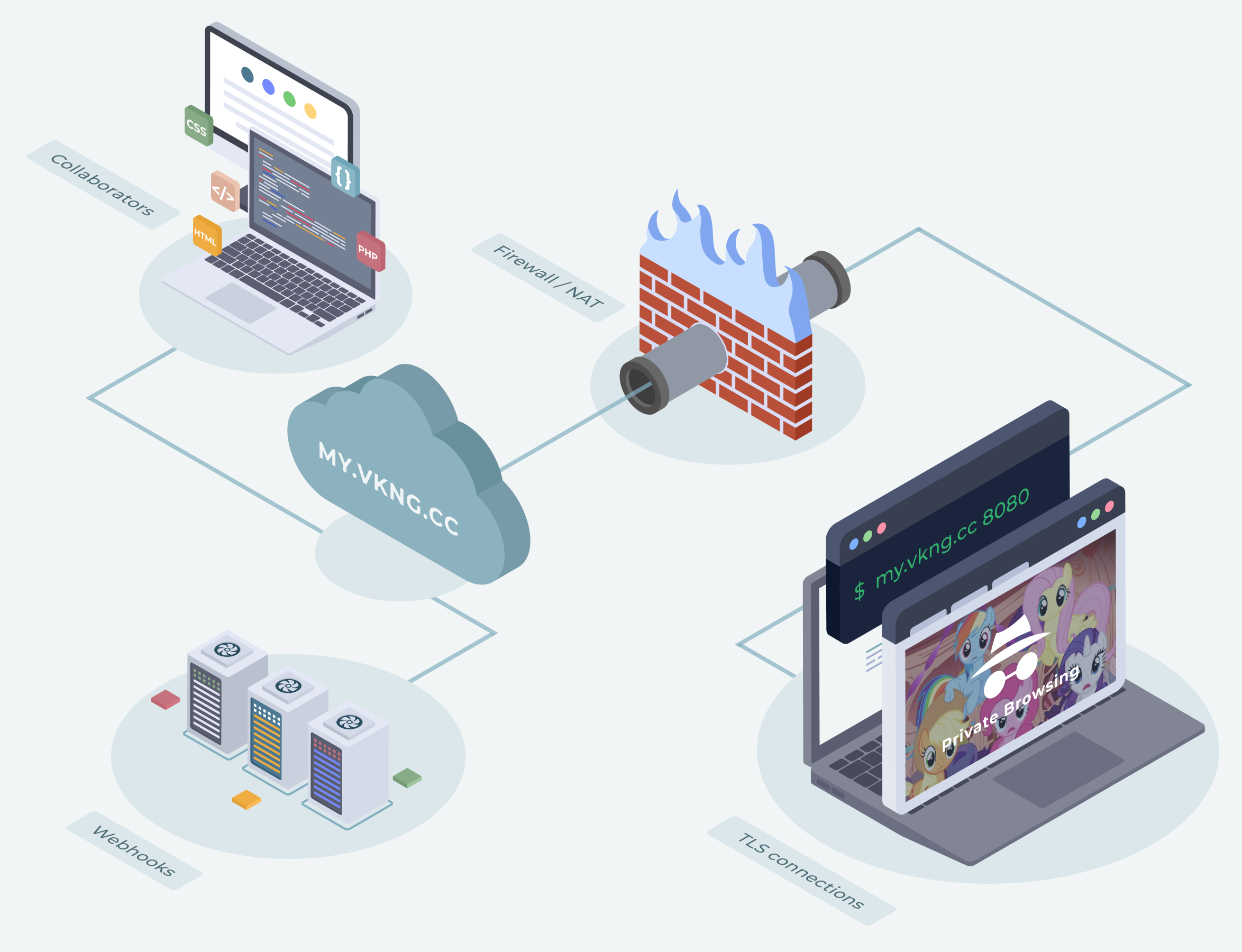
Our system is built on rules that are easy to expand. The core of the engine is Vikingo Satellite with Lua scripts and a model of different honeypots. Hackers think they are attacking a real application, but in reality it is our bait. We collect data on attacks and save them for further analysis.
Why is this for me?
You can view trending attacks, figure out which applications are most often trying to <strong>hack</strong> and protect your application by restricting access to IP addresses from which attacks are coming.
Is this project open source?
The core of the project is open source https://github.com/vikingo-project/vsat. The logic that lies inside for emulating applications and detecting attacks is closed.
Is this free?
Yes! All events are available to everyone. You always have the opportunity to view the statistics on the exploitation of a particular CVE.